Protect your Plesk server through Fail2Ban (Brute Force Protection tool)
Supported OS: Linux
Fail2Ban is a well known intrusion prevention software that protects computer servers from brute-force attacks.
With the introduction of Plesk Obsidian, the most recent version at the time of this guide, Fail2Ban has been installed by default.
If you have an older version of Plesk or are unable to upgrade to Plesk Obsidian, you can follow our guide that will walk you through installing it here.
Even when Fail2Ban is installed, it still needs to be enabled and configured to start protecting specific services (daemons) on your server.
You can follow the steps below to enable it:
Step 1
Access Plesk login via https://XXX.XXX.XXX.XXX:8443, replacing the X’s in our example with the IP address of your server.
Step 2
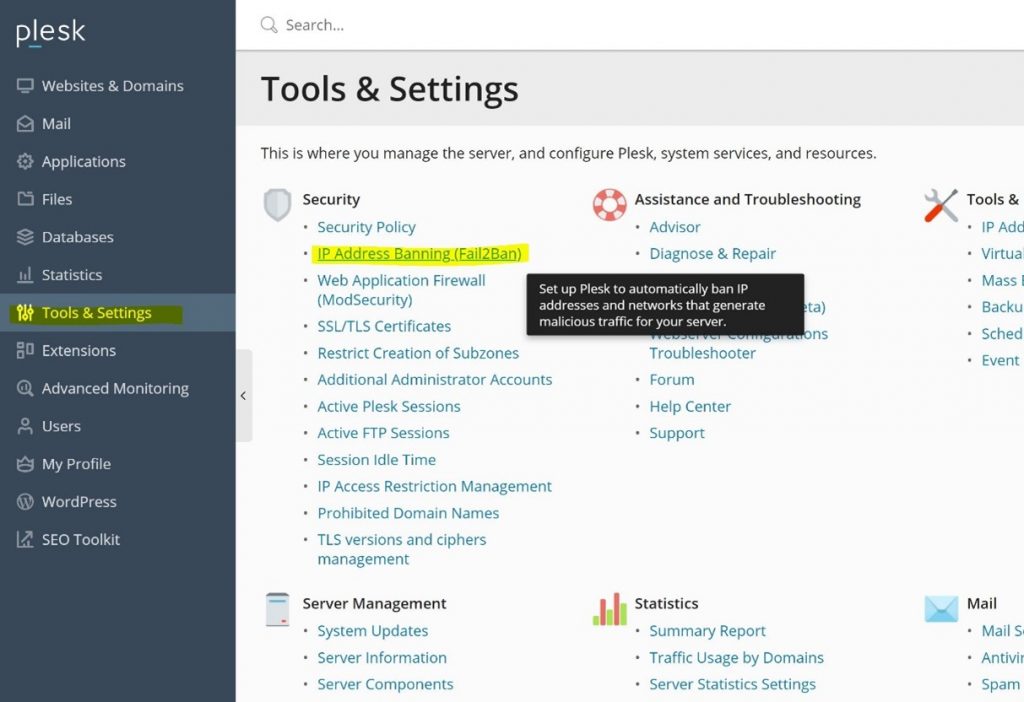
Select “Tools & Settings” from the menu on the left side of the page.
Step 3
Under the Security heading, locate and click on “IP Address Banning (Fail2Ban)” as show in the screenshot below:
Step 4
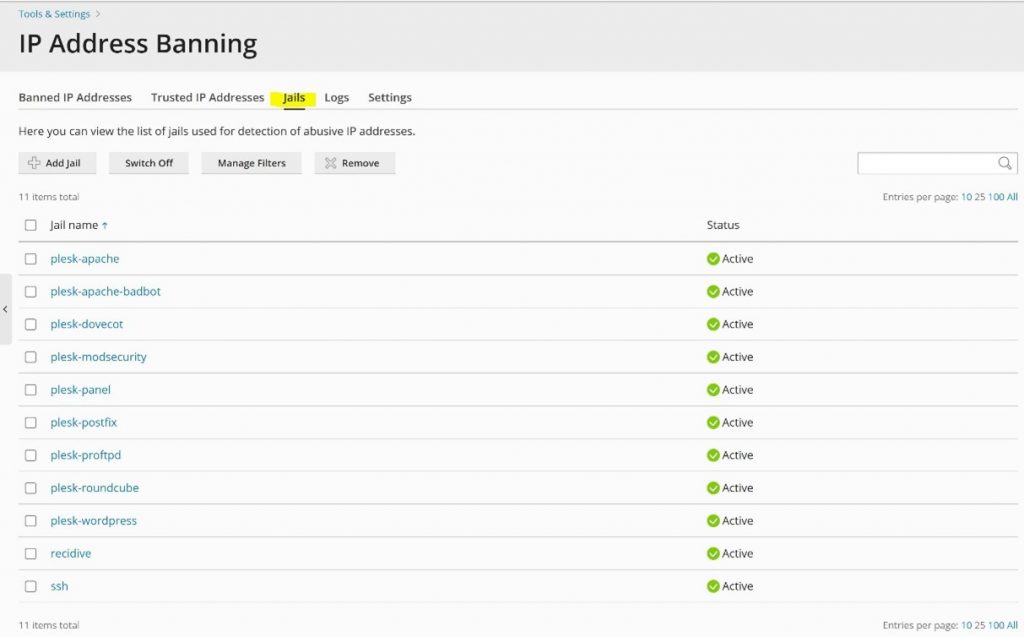
It is worthwhile looking at the Jails menu before you enable Fail2Ban.
Through Fail2Ban Jails menu, you can configure Fail2Ban to monitor specific services.
For reference, see the following screenshot:
Step 5
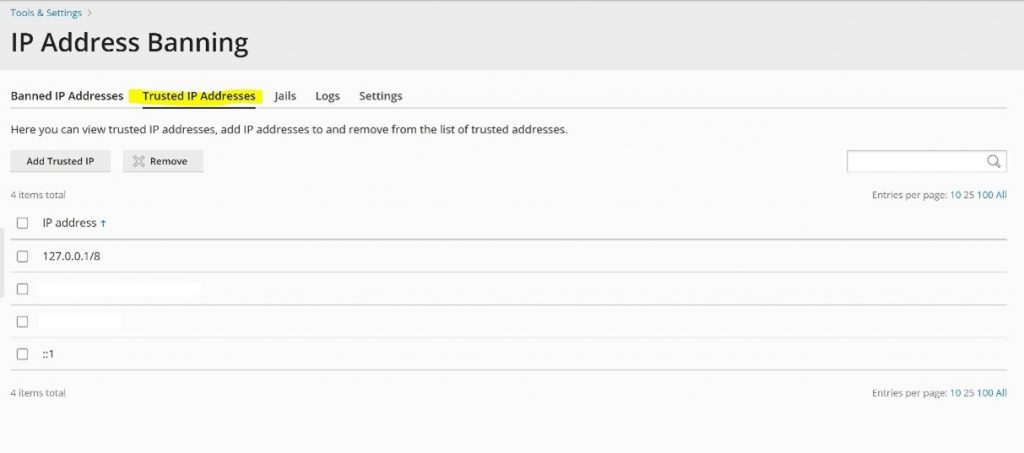
You can also add selected IP addresses to the Trusted IP addresses list so that they will not be banned by Fail2Ban.
This can be useful for users on your network. As an example, they can be added to this list to reduce the risk of them being blocked after an incorrect password is used in an attempt to log in.
Step 6
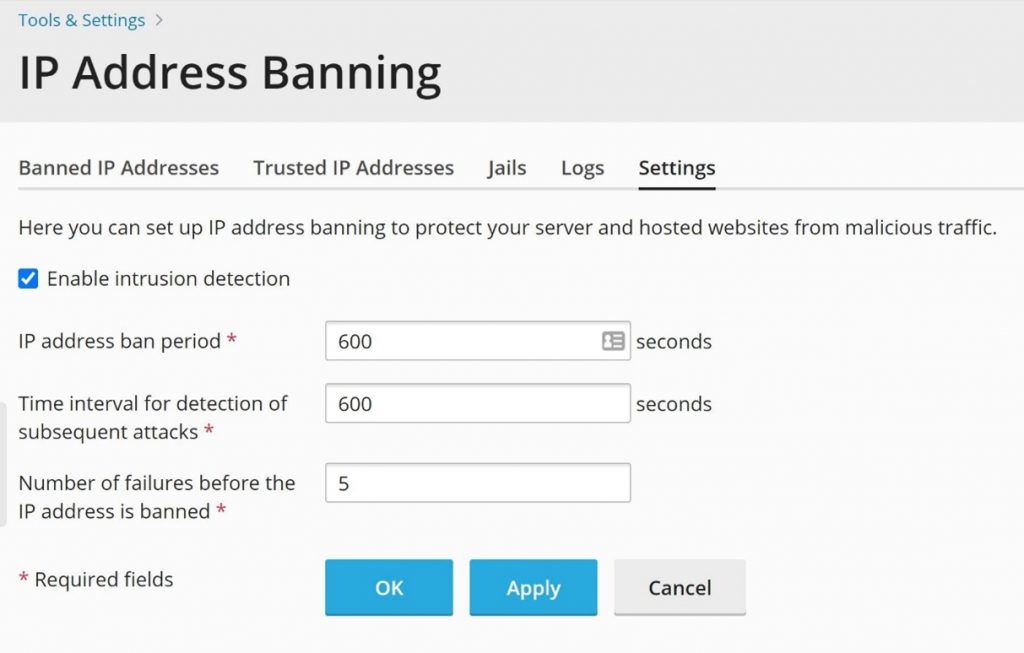
To enable Fail2Ban, click on “Settings“, then select “Enable intrusion detection” and then click on “OK“.
On the same page, you can see that it is possible to customise settings such as the ban period and the number of failures before the IP address is banned.
The following screenshot shows these options:
Step 7
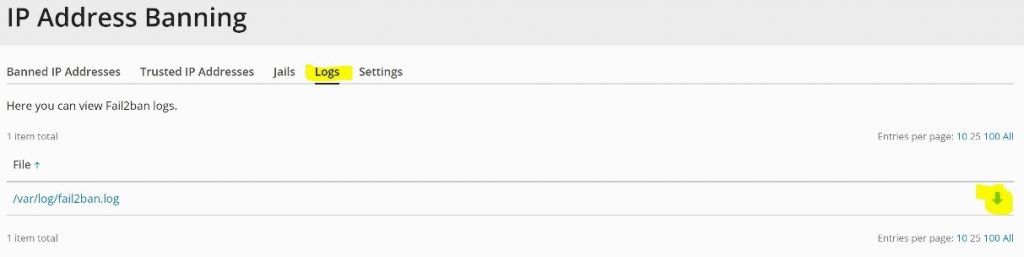
Fail2Ban activity is logged and you can check on this activity by analysing the log files which you can locate and download via the Plesk GUI.
The screenshot below shows the location of the log files: