Over the last 30 years or so, email has become an essential communication tool for businesses and individuals alike. But as with any system that relies on the internet, email does not come without risks. It’s often the first line of attack for hackers attempting to breach the corporate perimeter.
Because it’s so widely used, familiarity with email means that people may not be fully alert to the risks that it presents. So what can organisations do to keep their email systems secure?
Gone phishing
One of the most common forms of email attack is phishing. This is used in a number of different cybercrime scenarios. Most commonly it can be employed to trick people into revealing their sign in details for a website, notably banks and other sites dealing in financial transactions.
It can also be used to deliver malware by getting unsuspecting recipients to click on a link to an infected webpage.
The whole idea of phishing emails is that in order to work, they have to appear genuine. The old days of badly spelled, poorly formatted phishing messages are largely gone. This makes attacks more difficult to detect and requires staff to be on their guard when dealing with unexpected communications.

While security software can filter out some attacks, it’s training and awareness that is the key here. Staff in departments such as finance are especially likely to be targeted as cyber criminals try to get fake invoices or payment requests through.
It’s also important that people practice good email hygiene and are not tempted to share jokes or memes that could introduce risk. Similarly, sending files as attachments – particularly if unencrypted – should be discouraged.
Of course, there is another side to the phishing coin, which is when it’s your customers that are the intended victims of attack and your brand name that is being used to trick them. Phishing works because it exploits basic human psychological weaknesses. Cyber criminals know who to target and which buttons to press to get them to respond.
Protecting your brand
One of the ways of helping to prevent your customers from being duped in this way is to use DMARC (Domain-based Message Authentication, Reporting and Conformance). This is a system that validates whether an email is actually coming from the domain name it appears to be from.
Helping to eliminate attacks that ‘spoof’ the sender name to make it appear that they are coming from a legitimate source.
Many of the leading mail systems providers including Google, Microsoft and Yahoo have contributed to the DMARC specification so as more businesses adopt it, there should be an impact on the volume of phishing email received. Messages that fail DMARC authentication are either filtered to a spam folder or rejected completely and not delivered.
Senders get reports on messages sent using DMARC and can, therefore, see if any of their emails are failing authentication and adjust them accordingly.
An alternative to DMARC is Sender Policy Framework (SPF). This allows you to publish a record of all the domains your business uses to send email. Mail services check against this list and will treat any mail purporting to come from you but not from a listed domain as spam.
A third option is DomainKeys Identified Mail (DKIM). This uses public key encryption to verify the domain of an email and check that it hasn’t been tampered with in transit. The advantage of this is that the contents of the email are also secured.
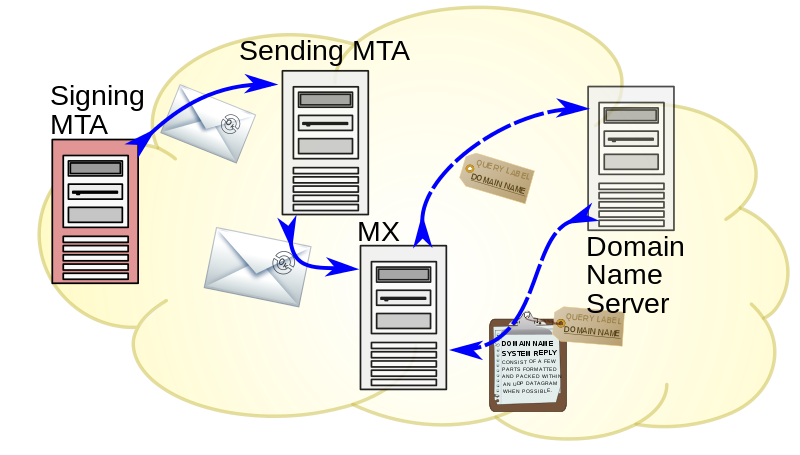
On the downside, you need to have a separate DNS entry and DKIM key for each service from which you send email. In addition to your own servers, this may include other services such as newsletter providers that send mail on your behalf. The Government offers guidance using mail authentication and other tips on keeping your email secure on its website.
Protecting your information
If you need to send confidential information via email then keeping it secure is essential. Email in its basic form is not secure and there’s a risk than any messages can be intercepted in transit.
Intercepting data can be a valuable resource for cyber crime organisations, not just in terms of financial information but because of intellectual property and other material you might want to keep under wraps.
We’ve mentioned DKIM above, but there’s another popular way of securing email message contents and that’s PGP. PGP (Pretty Good Privacy) has been around since the 1990s and has been continuously developed.
To use PGP you need appropriate client software, or a plug-in such as Mailvelope for use with online mail services including Gmail and Outlook. PGP works by exchanging public keys between senders which, in conjunction with a private key, allow the contents of an email to be encrypted and then unscrambled on receipt.